In today’s digital age, the concept of phone tracking has evolved from a simple tool for locating lost devices to a sophisticated system that can monitor an individual’s every move, online activity, and even personal preferences. As technology continues to advance, so does the potential for misuse, making it imperative for users to understand the intricacies of phone tracking and its implications. This introduction aims to provide a comprehensive overview of phone tracking, its various forms, purposes, and the potential risks and benefits associated with it.
A Brief History
The origins of phone tracking can be traced back to the early days of cellular technology. Initially, tracking was a means for service providers to ensure network coverage and handle calls efficiently. However, with the advent of smartphones and the proliferation of apps, the scope and capabilities of phone tracking expanded exponentially.
What is Phone Tracking?
Phone tracking, at its core, refers to the process of identifying the current location or tracking the movements of a mobile device, either by the device itself or by an external entity. This can be achieved through various means, including GPS, Wi-Fi, and cellular data.
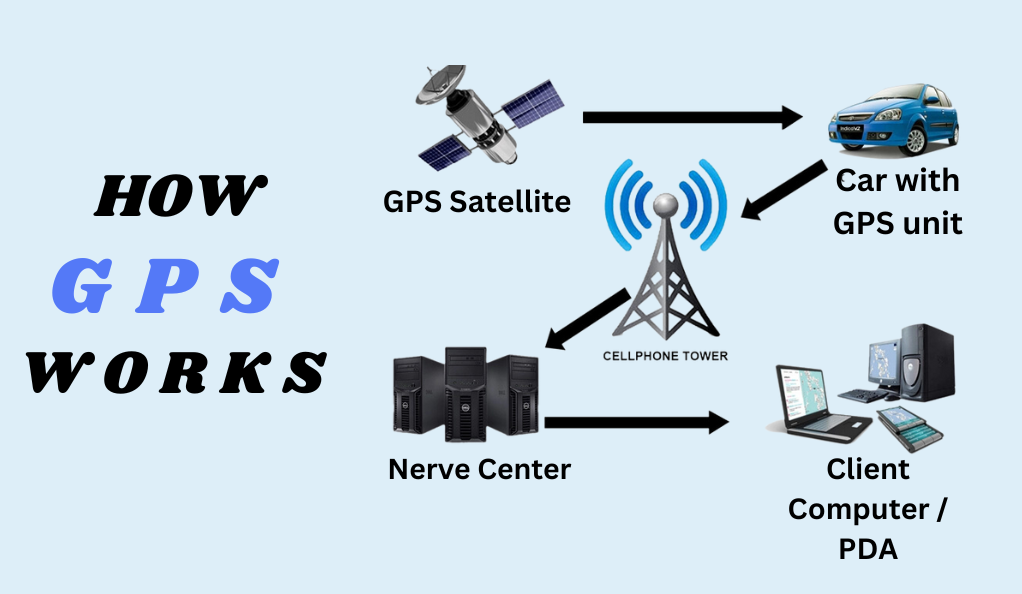
Types of Phone Tracking
- GPS (Global Positioning System) Tracking
This is the most accurate form of tracking, rel1ying on a network of satellites. It provides real-time location data and is the backbone of many navigation apps. - Wi-Fi and Cellular Data Tracking
In areas where GPS might be unreliable, phones can use nearby Wi-Fi networks or cellular towers to triangulate their position. This method is less precise than GPS but is effective in dense urban areas. - Bluetooth and NFC (Near-Field Communication)
These short-range communication technologies can also be used for tracking, especially in applications like finding lost items within a confined space.
The Dual-Edged Sword: Benefits and Risks
Benefits:
Phone tracking offers notable advantages, from revolutionizing navigation with GPS to enhancing safety during emergencies. Additionally, businesses utilize it to understand customer behavior, enabling more targeted marketing strategies.
Risks:
While phone tracking presents numerous advantages, it also comes with its set of risks. One of the primary concerns is the potential breach of privacy due to unauthorized tracking. This not only invades an individual’s personal space but can also lead to significant emotional distress. Furthermore, the misuse of personal data, whether sold or used for malicious purposes, is a growing threat in our digital age. Another subtle yet significant drawback is the over-reliance on tracking technology, which can diminish our innate navigation skills and make us overly dependent on electronic aids.
Understanding Phone Tracking
Phone tracking, once a concept limited to spy movies and high-tech espionage, has now become an integral part of our daily lives. From helping us navigate unfamiliar terrains to ensuring our loved ones are safe, tracking technology plays a pivotal role. However, to use it responsibly and protect oneself from potential misuse, it’s essential to understand its nuances.
How Phone Tracking Works
Understanding the mechanics of phone tracking can demystify its seemingly complex nature. Essentially, when a phone seeks to determine its position, it initiates a process by sending out a signal to nearby towers or satellites. In response, these towers or satellites send back their signals. The phone then calculates its location by analyzing the time it takes for these signals to return. Through advanced algorithms, this raw data undergoes refinement to provide users with a more precise and accurate location. This seamless interaction between the phone, satellites, and towers ensures that users can pinpoint their whereabouts in real-time, making tasks like navigation and location-based services efficient and reliable.
The Ethical Implications
As with any technology, phone tracking comes with ethical considerations. While it offers convenience and safety, it also raises concerns about privacy and consent. Unauthorized tracking or the collection of location data without explicit user permission is not only unethical but can also be illegal in many jurisdictions.
The Commercial Aspect of Phone Tracking
In the modern era, where data is often referred to as the “new oil,” phone tracking has emerged as a valuable tool for businesses, advertisers, and marketers. While consumers enjoy the conveniences offered by location-based services, the commercial world sees it as an opportunity to gain insights, enhance user experience, and drive revenue. This section delves into the commercial implications of phone tracking, shedding light on its benefits and potential pitfalls.
The Rise of Location-Based Marketing
Location-based marketing, a direct offshoot of phone tracking, allows businesses to target potential customers based on their geographical location. For instance, a coffee shop could send promotional offers to users who are within a mile radius, enticing them to visit. This hyper-targeted approach ensures that marketing efforts are directed at those most likely to convert, optimizing advertising spend.
Benefits to Businesses
Phone tracking offers businesses distinct advantages. By pinpointing a customer’s location, companies can provide tailored experiences and promotions, enhancing user engagement. This precise targeting optimizes advertising efforts, ensuring ads reach the most relevant audience. Additionally, the data gathered from tracking reveals insights into customer behaviors and preferences, aiding in strategic decision-making.
Data Collection and Monetization
Many free apps and services rely on data monetization as their primary revenue source. By collecting location data, these entities can build detailed user profiles, which are then sold to advertisers for targeted marketing. This model has proven lucrative, but it’s not without its controversies, especially concerning user privacy.
Potential Pitfalls and Ethical Concerns
While phone tracking offers a wealth of commercial opportunities, it’s not devoid of challenges and ethical dilemmas. One of the most pressing concerns is the potential invasion of user privacy. Collecting location data without clear and informed consent can be perceived as intrusive, leading to mistrust among consumers.
Additionally, the vast amounts of data amassed present a tempting target for cyberattacks, posing significant risks to user information security. Businesses also face the danger of over-reliance on location data, which might overshadow other valuable marketing strategies. As such, while the allure of phone tracking is undeniable, businesses must tread carefully, balancing their commercial interests with ethical considerations and user trust.
Dangers of Phone Tracking
In the age of digital interconnectedness, phone tracking has become a double-edged sword. While it offers undeniable conveniences, it also presents a series of risks that users must be aware of. This section delves deep into the potential dangers associated with phone tracking, emphasizing the importance of informed usage and protective measures.
Unwanted Surveillance
One of the most immediate concerns with phone tracking is the potential for unwanted surveillance. Whether it’s a nosy individual, a stalker, or even certain governmental entities, the ability to track someone’s movements in real-time can be misused in numerous ways, leading to breaches of privacy and personal security.
Data Breaches and Misuse
The collection and storage of location data introduce a myriad of potential risks, especially when these vast databases become targets for cybercriminals. When malicious entities gain unauthorized access, the implications can be far-reaching. For instance, with a detailed record of a person’s movements and routines, there’s an increased risk of identity theft.
Moreover, discerning when an individual is consistently away from their residence can provide opportunistic criminals with the perfect window for break-ins or financial fraud. Beyond these direct threats, there’s also the concern of data commoditization. Some companies, prioritizing profit over privacy, might sell this sensitive user data to third parties. This not only leads to unsolicited marketing but can also expose individuals to more sinister threats. In essence, while location data can be invaluable for various services, its potential misuse underscores the need for stringent security measures and ethical data handling.
Mental Health Implications
The pervasive nature of phone tracking can have profound effects on an individual’s mental well-being. The constant sense, or even just the suspicion, of being monitored can lead to heightened levels of anxiety. This ever-present feeling of surveillance can foster a sense of paranoia, making users overly cautious or prompting them to alter their natural behaviors to avoid being tracked.
Furthermore, an over-reliance on tracking apps and services can diminish one’s self-reliance, leading to a decreased trust in one’s natural navigation skills and instincts. In a world where technology is deeply integrated into our daily routines, it’s essential to recognize and address the potential psychological impacts of such tools, balancing the conveniences they offer with the mental health of users.
The Role of Legislation
As the implications of phone tracking become increasingly evident, many countries have taken legislative measures to address the associated challenges and protect user privacy. These legal frameworks often mandate that apps and services obtain explicit and informed consent from users before collecting any location data. This ensures that individuals are aware of and agree to the tracking activities.
Additionally, these laws emphasize the importance of data protection, obligating companies to implement robust security measures to prevent unauthorized access and misuse of the collected data. Furthermore, recognizing the importance of user autonomy, many legislations grant individuals the “Right to Erasure.” This provision allows users to request the permanent deletion of their data, ensuring they have control over their personal information. In essence, these legal measures aim to strike a balance between technological advancements and individual rights, fostering a safer and more transparent digital landscape.
Methods to Detect Phone Tracking
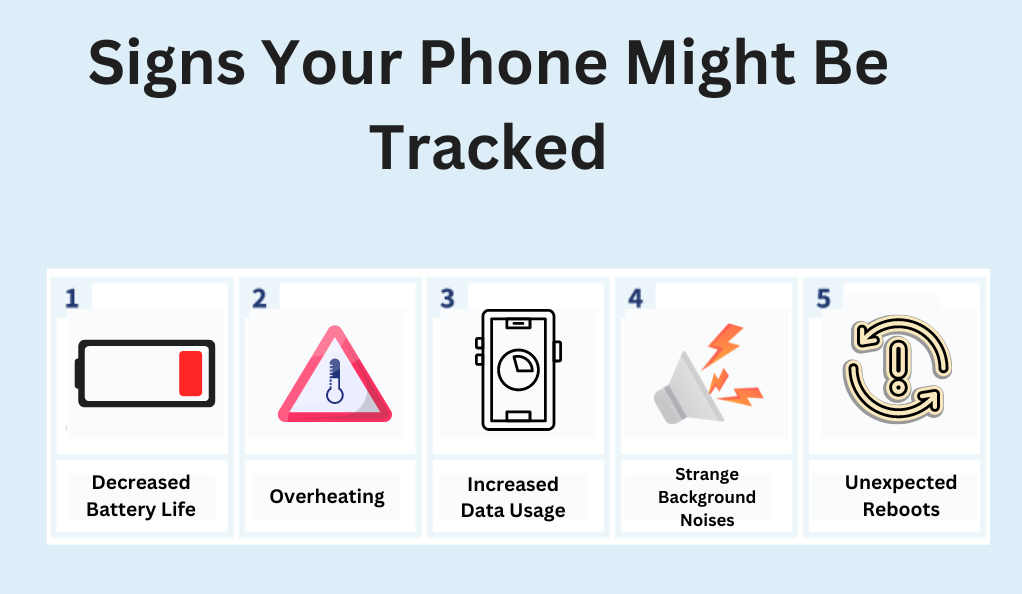
In an age where personal privacy is increasingly under threat, understanding how to detect phone tracking becomes paramount. While tracking can offer numerous conveniences, unauthorized surveillance can lead to a breach of privacy and potential misuse of personal data. This section will guide you through various methods to detect if your phone is being tracked, ensuring you remain in control of your digital footprint.
Signs Your Phone Might Be Tracked
Before diving into detection methods, it’s essential to recognize the potential signs that might indicate tracking:
- Decreased Battery Life: Tracking apps often run in the background, consuming more power.
- Overheating: Continuous data transmission can cause the phone to heat up.
- Increased Data Usage: Unexplained spikes in data usage can be a red flag.
- Strange Background Noises: During calls, unusual noises or echoes might indicate phone tapping.
- Unexpected Reboots: If your phone restarts without reason, it might be compromised.
Physical Inspection
One of the foundational steps in detecting phone tracking is a thorough physical inspection of your device. Begin by meticulously browsing through your list of installed apps. Any unfamiliar applications, especially those you don’t recall downloading, could be potential red flags indicating covert tracking software. Additionally, delving into your phone’s settings, particularly the permissions section, can provide insights. This area will display which applications have been granted access to sensitive information, including your location. By regularly monitoring and managing these permissions, you can ensure that only trusted apps have access to your data, reducing the risk of unauthorized tracking.
Use Anti-Spyware Tools
In the digital age, relying on specialized software can be a formidable line of defense against covert tracking. Numerous reputable anti-spyware tools have been developed for both Android and iOS platforms to address this concern. For instance, “Lookout” is a tool designed to detect and alert users about potential threats on their devices.
Similarly, “Avast Mobile Security” offers a comprehensive suite of features, including a privacy scanner that scrutinizes apps for suspicious behavior. Another notable mention is “Malwarebytes,” which is adept at scanning for and removing potential spyware from your device. By incorporating such tools into your regular device maintenance routine, you can bolster your defenses against intrusive tracking software, ensuring your privacy remains intact.
Network Analysis
Analyzing your device’s network interactions offers another layer of insight into potential tracking activities. Utilizing Wi-Fi scanners, such as Wireshark, allows users to monitor the flow of network traffic, highlighting any unusual or suspicious data transmissions that might indicate covert tracking. Additionally, firewall applications, like NetGuard for Android, serve a dual purpose. Not only do they provide a protective barrier against malicious intrusions, but they also grant users the ability to monitor and control which apps can access the internet. By keeping a close eye on network activities and restricting unnecessary access, users can further safeguard their devices from unwanted tracking and potential breaches.
Professional Help
If suspicions persist despite individual efforts, seeking external expertise can be a prudent course of action. Tech experts, equipped with specialized knowledge and tools, can conduct a comprehensive examination of your device, identifying and addressing any covert tracking software that might have been overlooked. Their in-depth analysis can provide peace of mind, ensuring that your device is free from unwanted surveillance. Moreover, if there’s a belief that tracking is occurring unlawfully, it might be essential to escalate the matter by involving law enforcement. Authorities can investigate the issue further, ensuring that any illegal tracking activities are promptly addressed and that your privacy rights are upheld.
Effective Ways to Prevent Phone Tracking
In our interconnected digital age, the potential for phone tracking—both authorized and unauthorized—has grown exponentially. While there are benefits to location-based services, the risks associated with unwanted tracking are undeniable. To maintain privacy and security, it’s crucial to understand and implement measures to prevent unwarranted phone tracking. This section will guide you through various strategies to safeguard your device and personal data.
- Understanding App Permissions
One of the primary gateways to phone tracking lies in the permissions granted to the apps installed on your device. Every application, upon installation or during use, requests access to certain features of your phone, including location services. It’s imperative to regularly review these permissions, ensuring that only essential apps have access to sensitive data. By scrutinizing and revoking unnecessary permissions, especially those related to location access, you can significantly reduce the risk of unwanted tracking.
Additionally, it’s advisable to exercise caution when downloading new apps. Opting for applications from reputable sources and developers, coupled with thorough research and review reading, can prevent the inadvertent installation of malicious tracking software.
- Limit Location Services
Location services, while offering convenience, can also be a potential avenue for unwanted tracking. To mitigate this risk, it’s advisable to exercise control over when and how these services are accessed. Turning off the location setting when it’s not actively needed can significantly reduce the window of opportunity for unauthorized tracking. For applications that necessitate location access, such as navigation or weather apps, opting for the ‘While Using the App’ permission setting ensures that your location is accessed only when the app is in active use. This not only conserves battery life but also adds an additional layer of privacy, ensuring that background tracking is minimized.
- Stay Updated
In the ever-evolving landscape of technology, staying updated is a crucial defense against potential tracking threats. Regularly updating your phone’s operating system and the apps you use is more than just accessing new features; these updates often come with security patches designed to fix vulnerabilities that could be exploited for tracking or other malicious purposes. Additionally, it’s beneficial to stay informed about the latest developments in tracking methods and countermeasures. By keeping oneself abreast of the newest techniques and prevention strategies, one can ensure a proactive stance against unwanted surveillance, fortifying the device against emerging threats.
- Use Encrypted Communication Tools
In today’s digital age, ensuring the privacy of your communications is paramount. Leveraging encrypted communication tools can provide an added layer of security against potential eavesdroppers and trackers. Messaging apps such as Signal and WhatsApp, for instance, offer end-to-end encryption, ensuring that only the sender and recipient can access the content of the messages, keeping them shielded from any prying eyes.
Additionally, using a Virtual Private Network (VPN) can be instrumental in safeguarding your online activities. A VPN masks your actual location by routing your internet connection through a server in a different location, making it considerably more challenging for trackers to pinpoint your exact whereabouts. By integrating these encrypted tools into your daily communication habits, you can significantly enhance your digital privacy and security.
- Physical Precautions
Physical measures complement digital safeguards in the fight against phone tracking. Using covers for your phone’s camera and microphone can prevent covert spying. Additionally, activating airplane mode not only saves battery but also temporarily stops all potential tracking communications, offering a brief respite from digital surveillance.
- Educate and Advocate
Empowerment in the realm of digital privacy stems from knowledge and advocacy. By educating oneself about the intricacies of digital surveillance and the tools available for protection, individuals can make informed decisions about their device usage and data sharing. But beyond personal education, there’s a broader responsibility to advocate for collective digital rights and privacy. Supporting organizations and movements that champion these causes not only benefits the individual but also contributes to a larger societal shift towards a more secure and private digital landscape.
Advanced Tips for Enhanced Privacy
In the digital age, where data breaches and cyber threats are becoming increasingly common, it’s essential to go beyond basic privacy measures. For those who prioritize their digital privacy and want to ensure maximum protection against potential threats, here are some advanced tips to fortify your defenses.
Multi-Factor Authentication (MFA)
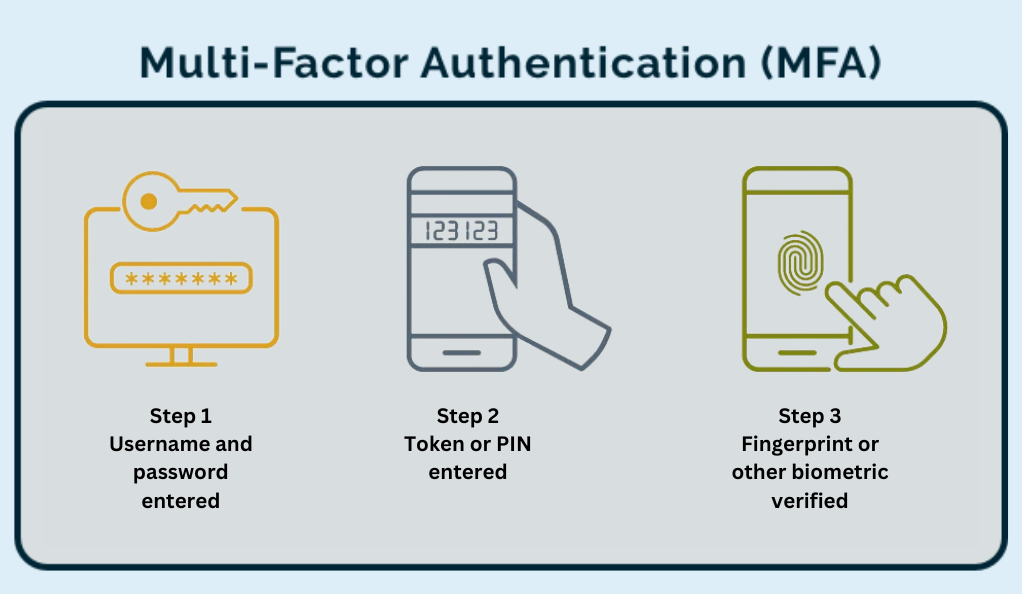
Multi-Factor Authentication (MFA) stands as a robust line of defense in the realm of digital security. This authentication method goes beyond the traditional password, requiring users to provide multiple forms of identification before granting access to an account. The strength of MFA lies in its layered approach; even if a malicious entity manages to obtain a user’s password, they would still face the hurdle of another verification layer, be it a text code, biometric data, or a security token. By integrating MFA into their security protocols, individuals can significantly enhance the protection of their online accounts, reducing the risk of unauthorized access.
Use a Dedicated Privacy Browser
Dedicated privacy browsers like Tor and Brave offer enhanced online protection. Designed to block unwanted trackers, they ensure users browse anonymously. By prioritizing user privacy, these browsers provide a secure and efficient browsing experience, making them essential tools for those valuing their digital confidentiality.
Regularly Audit App Permissions
Consistent oversight of app permissions is a proactive measure to safeguard one’s digital privacy. By conducting monthly or bi-monthly checks on the permissions granted to apps, especially those accessing sensitive features like location, camera, or microphone, users can ensure that no application oversteps its boundaries. This regular audit not only prevents potential tracking but also ensures that users have full control over which apps can access specific functionalities on their devices. In essence, a routine audit of app permissions is a simple yet effective way to maintain control over one’s digital environment.
Use Encrypted Cloud Storage
As the reliance on cloud storage grows, ensuring the security of data stored in the cloud becomes paramount. Encrypted cloud storage solutions, such as Tresorit and Mega, offer an added layer of protection. Before data is uploaded to the cloud, it’s encrypted, rendering it unreadable to anyone without the appropriate decryption key. This means that even if there’s a breach or unauthorized access, the data remains secure and unintelligible. By opting for encrypted cloud storage, individuals can enjoy the convenience of the cloud while ensuring their sensitive data remains protected from potential threats.
Stay Informed About Zero-Day Vulnerabilities
Staying abreast of zero-day vulnerabilities is crucial in the ever-evolving digital landscape. These vulnerabilities refer to flaws in software that are unknown to the vendor, leaving no time (“zero days”) for a fix before potential exploitation. Such vulnerabilities can be exploited by cybercriminals to gain unauthorized access or cause harm. By subscribing to tech news outlets or forums that provide timely updates on these vulnerabilities, individuals can be better prepared and take necessary precautions. Being informed allows users to act swiftly, applying patches or avoiding certain software until a fix is released, ensuring their digital assets remain secure against emerging threats.
Limit Digital Footprints
In the vast expanse of the digital world, every action, from browsing a website to liking a post, contributes to one’s digital footprint. To bolster privacy, it’s essential to minimize this footprint. Regularly clearing cookies, using pseudonyms online, and employing a VPN even for routine browsing can significantly reduce the amount of personal data left exposed on the internet. These measures not only shield users from targeted ads but also from potential malicious actors who might exploit this data. By actively limiting one’s digital footprint, individuals can navigate the online realm with greater anonymity and security.
Conclusion
In today’s digital era, where every click and scroll can be monitored, the importance of safeguarding one’s privacy cannot be overstated. From understanding app permissions to limiting digital footprints, each step taken towards enhanced privacy is a stride towards reclaiming control over personal data. As technology continues to evolve, so too will the methods to exploit it. Therefore, staying informed, proactive, and vigilant is not just a choice but a necessity. By adopting the measures discussed and continuously adapting to new challenges, individuals can ensure a safer, more private digital experience, striking a balance between the conveniences of modern technology and the sanctity of personal privacy.
At bitvestment.software, our commitment is to deliver unbiased and reliable information on subjects like cryptocurrency, finance, trading, and stocks. It's crucial to understand that we are not equipped to offer financial advice, and we actively encourage users to conduct their own comprehensive research.
Read More